Hackers Are Using MailChimp to Spread Malware
 As most of you probably know MailChimp is a widely used and well respected email newsletter and marketing automation service.
As most of you probably know MailChimp is a widely used and well respected email newsletter and marketing automation service.
It’s not a news that hackers tend to focus on popular services, and that’s exactly what we noticed in at least two different Italian malware campaigns in the last week, where they jumped on MailChimp popularity to spread malware sending out emails containing malicious links. What is noticeable is the questionable MailChimp security approach in response to those incidents.
Let’s start with a little more of context describing the malware campaigns and the steps we took.
The first round of phishing emails containing links to malware pretended to be a notification for taxes to be paid within the 1st of February. The subject was “F24 ACCONTI-Codice Tributo 4034”. F24 is an Italian tax form. “Codice Tributo” stands for “Tax Code” and “Acconti” are tax payments made in advance, before the actual amount due for the year is calculated.
The target was clearly Italy and a single MailChimp account has been used in this round, the emails contained links to the MailChimp subdomain fallriverproductions.us16.list-manage.com. Apparently this is a MailChimp account that has been compromised and used to deliver the malware.
What’s important to note, though, is that the recipients of these phishing emails aren’t the original recipients of the MailChimp account. Whoever compromised the account uploaded their own list of email addresses which included harvested addresses and also spamtraps.
Here is a sample of the first round of MailChimp phishing emails:
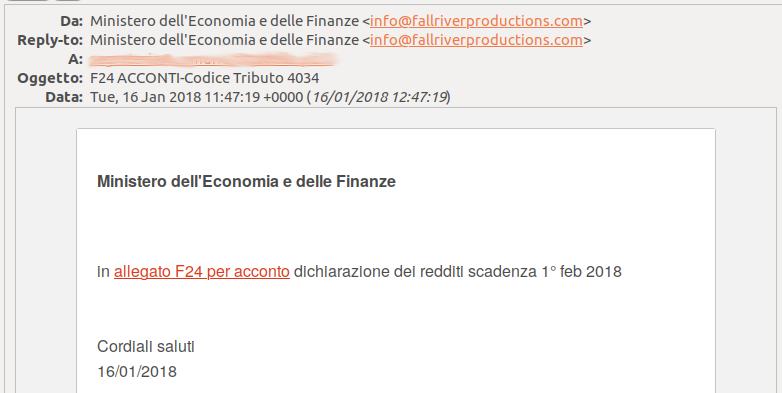
MailChimp phishing sample, pretending to come from the Italian Ministry of Finance. The friendly-from is [email protected]. The MailChimp Feedback-ID is 76673258:76673258.249363:us16:mc
Most of these emails slipped through email filters as they were originating from a hacked account on a respectable service, and only an advanced protection like our URLSand Protection was effective protecting users that clicked on the malicious links, but obviously this is not enough!
MailChimp has been contacted and the abuse reported, but maybe due to timezone issues, a huge amount of emails had already been sent when MailChimp abuse team managed to stop the activity.
At this point a second round of phishing emails started, this time pretending to be a notification for taxes to be paid within the 5th or the 6th of February. The subject was either “Codici Tributo Acconti” or “f24 accontiCodici Tributo”. Two MailChimp accounts have been used in this round, the emails contained links to these MailChimp subdomains: amber-kate.us3.list-manage.com, lc-hc.us16.list-manage.com. Again, these seem to be MailChimp accounts that have been compromised and used to deliver the malware.
Here are the samples for the second round:

MailChimp phishing sample, pretending to come from the Italian Ministry of Finance. The friendly-from is [email protected]. The MailChimp Feedback-ID is 24073083:24073083.1514657:us3:mc
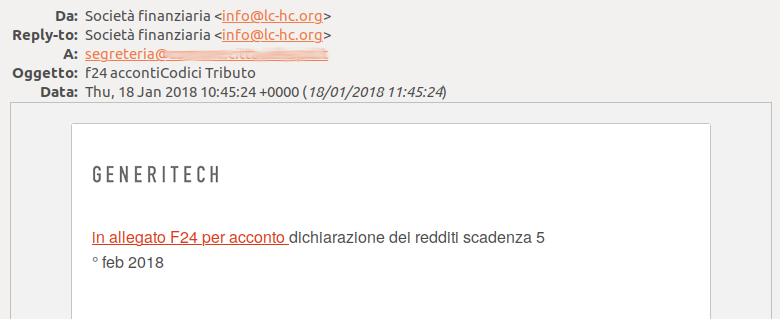
MailChimp phishing sample, pretending to come from a financial company. The friendly-from is [email protected]. The MailChimp Feedback-ID is 79510402:79510402.290027:us16:mc
Apparently the hackers got control of multiple MailChimp accounts and as soon as one got suspended they started using another one. Everytime the hackers managed to upload huge lists of recipient email addresses to which deliver the malware email campaign. Apparently this didn’t trigger abuse prevention alerts.
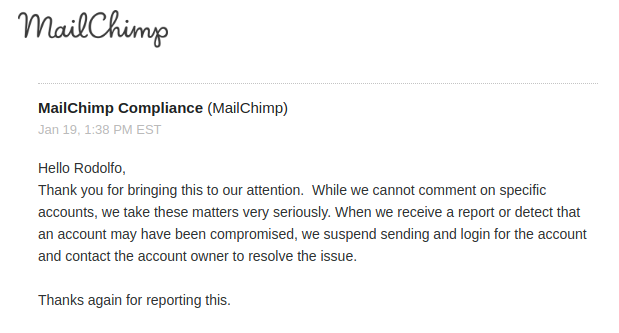
We tried to contact MailChimp on multiple channels: two different abuse forms and twitter. We reported the abuse identifying the compromised accounts and we proposed to set-up a communication channel to quickly share intelligence: we would quickly report to MailChimp new abuses and MailChimp would quickly report to us new compromised accounts so that we could proactively protect our customers without penalizing all of the MailChimp traffic. Everytime we got template responses like the following one.
The problem in being reactive in this way (with additional delays related probably to timezone differences) is that once the abuse is reported and the account is suspended, all of the malicious emails are already gone.
MailChimp doesn’t require double opt-in (it’s not even enabled by default). Every customer can upload lists of recipients (even huge ones) and send emails without the recipient having proven consent.
The incident shows that hackers will likely use whatever distribution channels they can in an attempt to spread their malware and turn a profit and surely MailChimp is not the only one.
Even if advanced URL sandbox services like the one offered by Libra Esva actively help protecting from these kind of attacks, we expected more from such a well respected and widely used service! At least in the management of the incident.
The company would not say what the exact issue was, but MailChimp’s statement was simply that they closed the compromised accounts, with a long delay since our first submission and not showing any collaboration in mitigating these problems to happen again.