Fresh phishing served with AES obfuscation
Obfuscated phishing sites are nothing new (on the same matter check this article Web obfuscation technique using invisible spans ) but the use of AES in an attempt to evade detection from automated detection tools like our URLSand Sandbox service, is not very common.
Despite AES and encryption in general is not a newbie argument, I am surprised how easily this approach can be adopted by anyone with a basic programming knowledge.
The only thing needed is a Javascript library, freely available for download from Movable Type Scripts.
By including this library in your page you can then serve your encrypted webpage, with a few lines:
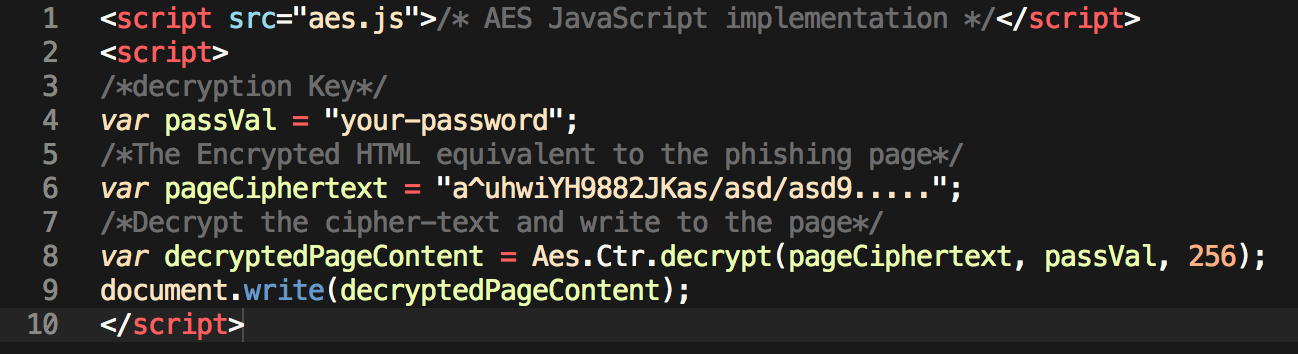
To explain the above lines:
Line 1) includes the JavaScript AES implementation, which it calls with the embedded password defined at Line 4) and embedded encrypted data at Line 6). The decrypted phishing content is then dynamically written to the page using document.write() after calling the decryption function at Line 8).
This process happens almost instantly when the page is loaded and once decryption is complete, the phishing site is shown as normal.
Note that the use of AES here is very basic, and there is no attempt made to hide the key or anything else. But I would not be surprised if this kind of attacks will become more sophisticated in the near future!
Eng.Paolo Frizzi
