Email Archiver Realese 19.10
Abbiamo da poco rilasciato la release 19.10 dell’Email Archiver Libraesva.
Cosa prevede?
- Aggiornamento automatico della licenza
- Aggiunto supporto a nuovi tipi di volume (Azure, Wasabi, Digital Ocean, Scaleway, Google Cloud, Rackspace, OVH, UKCloud, OpenStack – Swift)
- Aggiunto supporto al bloccaggio dell’aggiornamento automatico + possibilità di cambiare canale di aggiornamento (stabile o beta)
- Aggiunto filtro per data aggiuntivo nella configurazione di un job di esportazione
- Migliorato logging import batch da Exchange
- Aggiunto conteggio rate di deduplica
- Abilitato caching per aumentare la velocità e la responsiveness dell’archiver
- Aumentato TTL refresh token (API)
- Aggiunto supporto al tema scuro per il plugin di outlook
- Aggiunto supporto a check sugli header custom nelle archiving rules
- Aggiunta condizione di uguaglianza nelle ricerca avanzate
Email trojan horse: application/html entity
We just discovered a new trick that is currently being used to slip malicious html files through email security solutions and, in some cases, through antivirus engines.
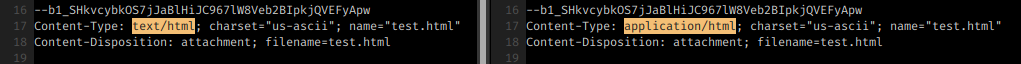
The trick is quite simple: declaring an email entity as “application/html” instead of “text/html”. “application/html” is an invalid type and this allows it to slip through some checks.
Background
Emails are composed of many “parts” called “entities”. Each entity has a content-type header that declares the type of it’s content (the textual or the html portion of the email, the images contained in the message, the attachments which can be of many different file formats). For example the html portion of the mail has content-type “text/html”, the text part is declared as “text/plain”, an image can be “image/png”, an attached office document can be “application/msword”, and so on. There is a list of valid types and “application/html” is not among those.
What happens if you declare an invalid content type? It depends. Email clients try to be helpful and tend to consider as valid the types they don’t know, but security solutions and antivirus engines may behave differently. They make specific security check that depend on the content and when faced with a content type they don’t know in some cases the end up ignoring or not analyzing properly the content of these entities. At least this is what happens with the entity type “application/html” that we tested.
Samples in the wild
The samples found in the wild are delivering html files that, as soon as they are opened, redirect to a malicious site (through a meta tag). These very small one-line html files are attached to malicious emails inside an entity of an invalid type “application/html” instead of the correct type “text/html”. All the email clients we tested (including the major webmail services) show these files as normal attachments but all the email security filters we tested (including those of the major wemail services) could not find malicious links contained in these html files if the entity was “application/html”. While they did detect them if contained in a normal “text/html” entity, they could not detect them if the entity type was changed to “application/html”. This trick is actively being used in the wild, this is why it is appropriate to go public with these findings.
Our testing
In order to assess how these entities are managed by email services and clients, we created two email samples with an html attachment containing a link to a malicious website. One of the samples has the entity type changed to “application/html” instead of the normal “text/html”. This is the only difference between the two samples.
The sample with the “application/html” entity was delivered as clean in the inbox of all the systems we tested (including the major email providers) while the very same email with the entity of type “text/html” was correctly classified as dangerous. Some checks are clearly missing when the entity type is “application/html”.
All it takes to create a “stealth” entity is to change the word “text” into the word “application” in the content-type declaration.
All the email clients (including major webmail services) allowed the user to open the html file contained in the “application/html” entity.
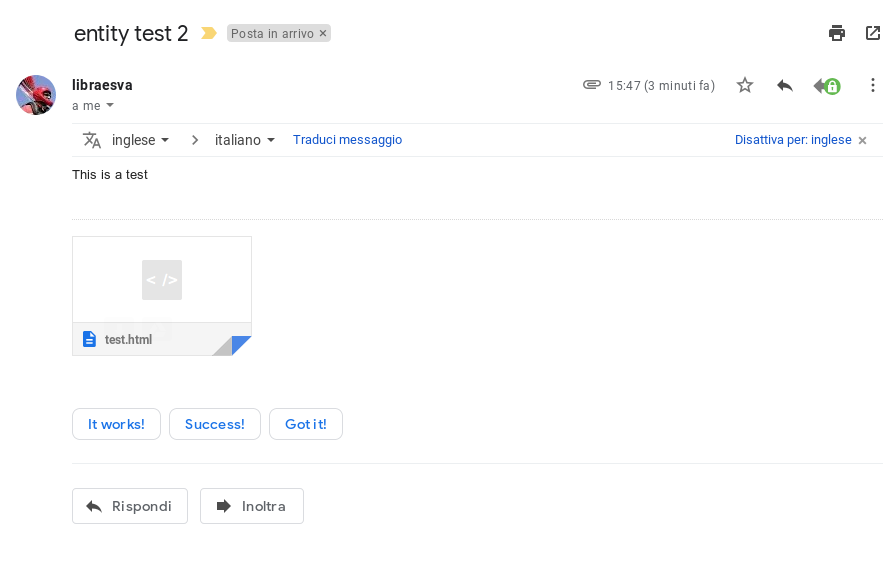
Here is the malicious html file inside an application/html entity sent to Gmail:
Clicking on the attachment, it is displayed and offered for clicking.
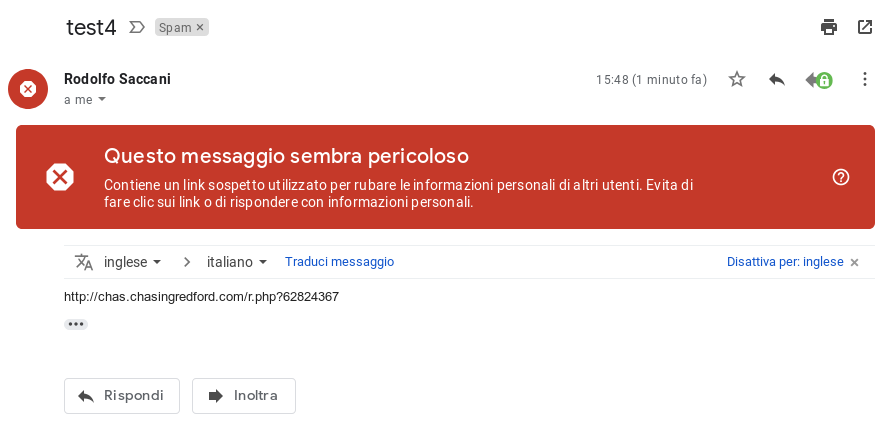
Here is the same malicious html file sento to Gmail in a normal text/html entity:
The text/html entity is properly analyzed and classified as dangerous, the application/html entity is not.
Tests with actual malware
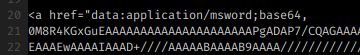
We performed a second test, by embedding a real sample of emotet in the html attachment (inside an href tag). With this sample the results varied: major email providers correctly detected the threat while some email filtering solutions didn’t.
The image above shows how we embedded emoted inside the html file.
These samples have been also tested with major and widely used antivirus engines: some of them did not inspect the “application/html” entity even if they could correctly detect the same sample in a “text/html” entity.
The target of this post is to raise awareness so there is no point in naming products here. We just show a test performed with an opensource antivirus engine.
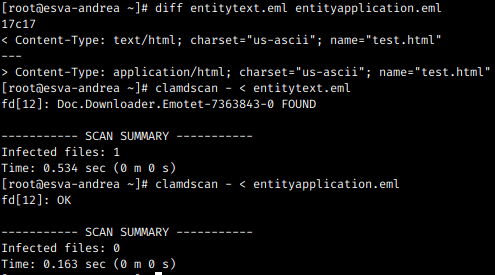
In the previous image we have two samples containing emotet embedded in the html file.
entitytext.eml had a normal “text/html” entity while entityapplication.eml had an entity of type “application/html”. The first command (diff entitytext.eml entityapplication.eml) shows that the only difference between the two emails is the word “text” replaced with “application” in the content-type declaration.
As you can see the antivirus detected emotet in the first sample and didn’t detect it in the second. This test used clamav but the same test with major commercial antivirus engines produced similar result.
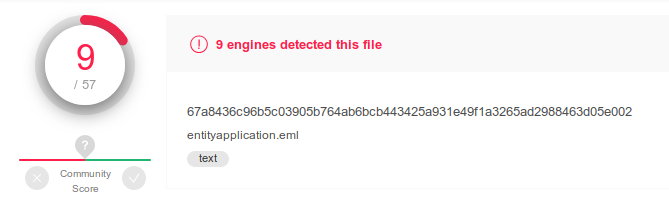
The sample entityapplication.eml uploaded on virustotal has been classified as malware by 9 engines on 57:
Conclusions
From an email security gateway point of view, blocking emails containing entities of type “application/html” is probably the wisest thing to do and this is what we are currently doing.
This is clearly an attempt to evade security inspection by pretending to be some kind of unkown application-specific data, inducing to perform only broad and general security checks (for example clamav does not decode base64-encoded data embedded in the href tag if declared as “application/html”) while, at the same time, inducing the email client to offer the file to the user as a normal html attachment.
An attempt to evade analysis is a strong signal about the malicious intention of the sender and should be penalized accordingly.
This threat has been added to our email security tester, a tool to assess the performance of emails security protections. This means that you can easily test, right now, whether you are protected or not from this and other common email threat vectors.
Five things admins forget when using Libraesva ESG
I get it, you’re a hot shot Libraesva ESG admin who knows everything about the system, but even the best of us make mistakes and forget the basics, even me! In a recent certification course we held in the UK we discovered some fairly obvious shortcomings in basic configuration and management of the solution that most admins adhere to and we thought right now is a great time to inform you of them, so you can continue being a pro Libraesva ESG admin.
- Libraesva ESG does the leg work for you
Libraesva ESG is built from the ground up to be set and forget meaning you really don’t need to reinvent email security, some of the first things administrators like to do is change the anti-spam scoring, the default rule sets and even switch off the sandboxes (I know, weird right!?). However, this isn’t optimal or even required at all.
Libraesva ESG comes setup out the box in its most optimal and secure mode, it links directly back to Libraesva HQ to get up to date analysis statistics and rule sets so you don’t have to, at most the Libraesva system will need input from users in the quarantine section and threat submissions. The Libraesva team are constantly updating the ESG platform, rule sets, and our security engines to make your life easier and lessen the management load of you and your admins.
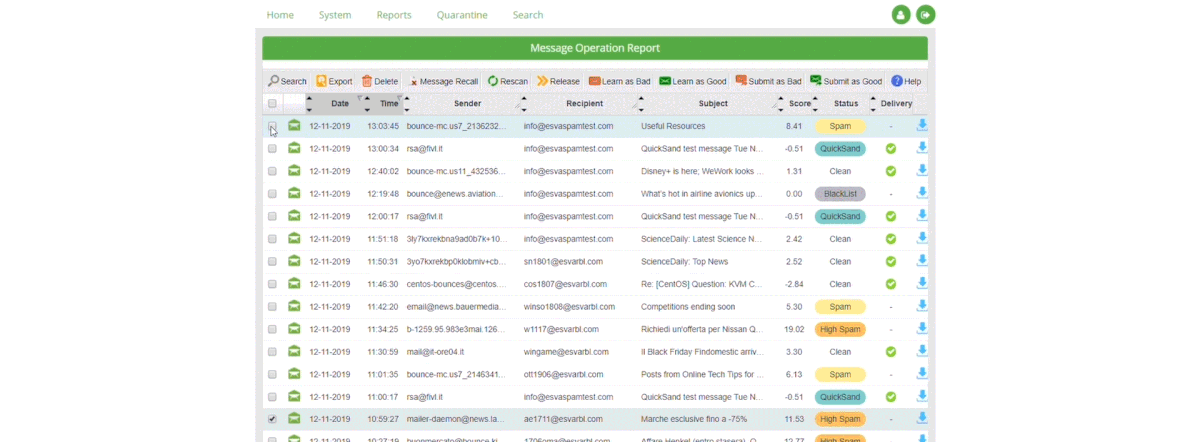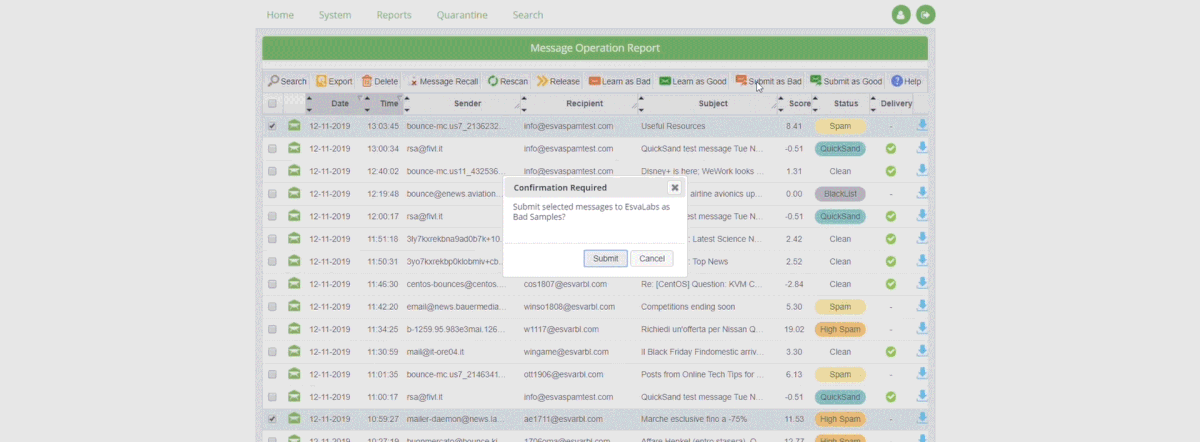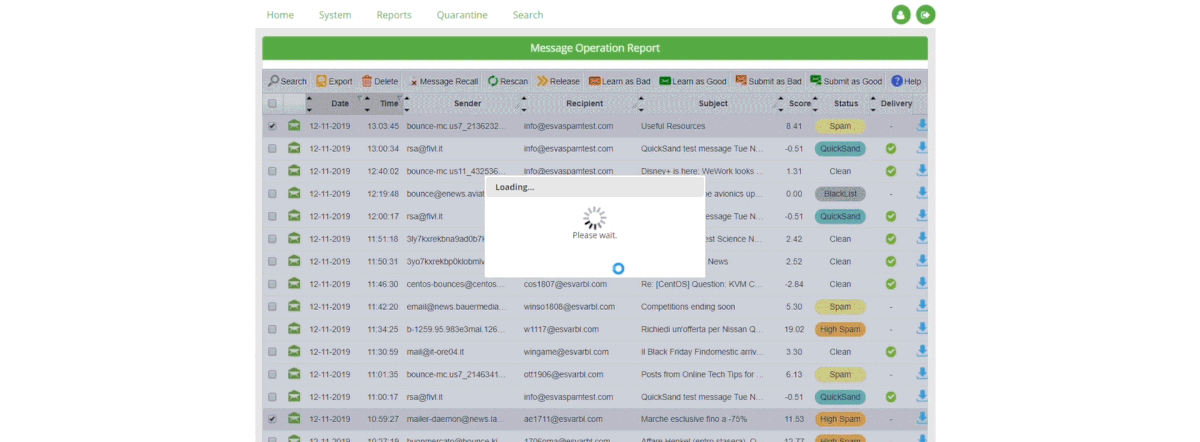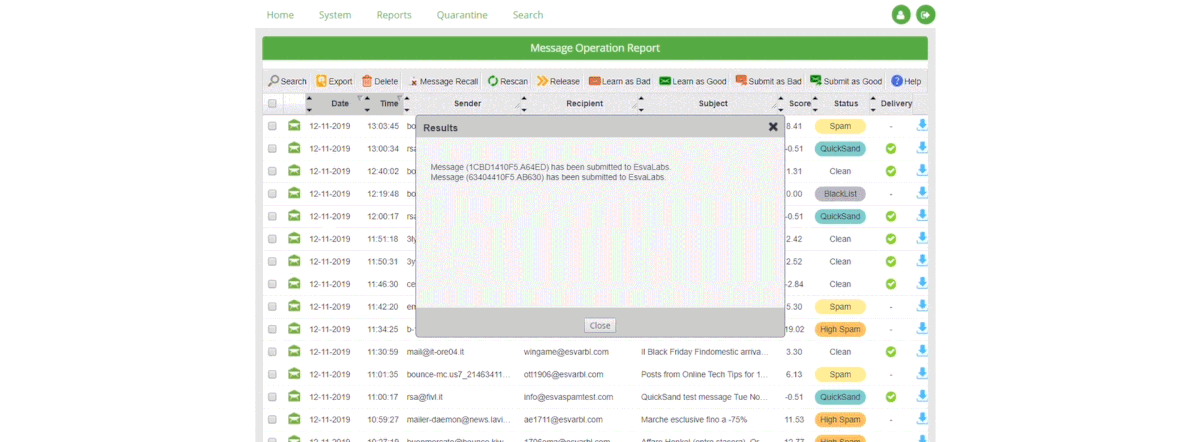
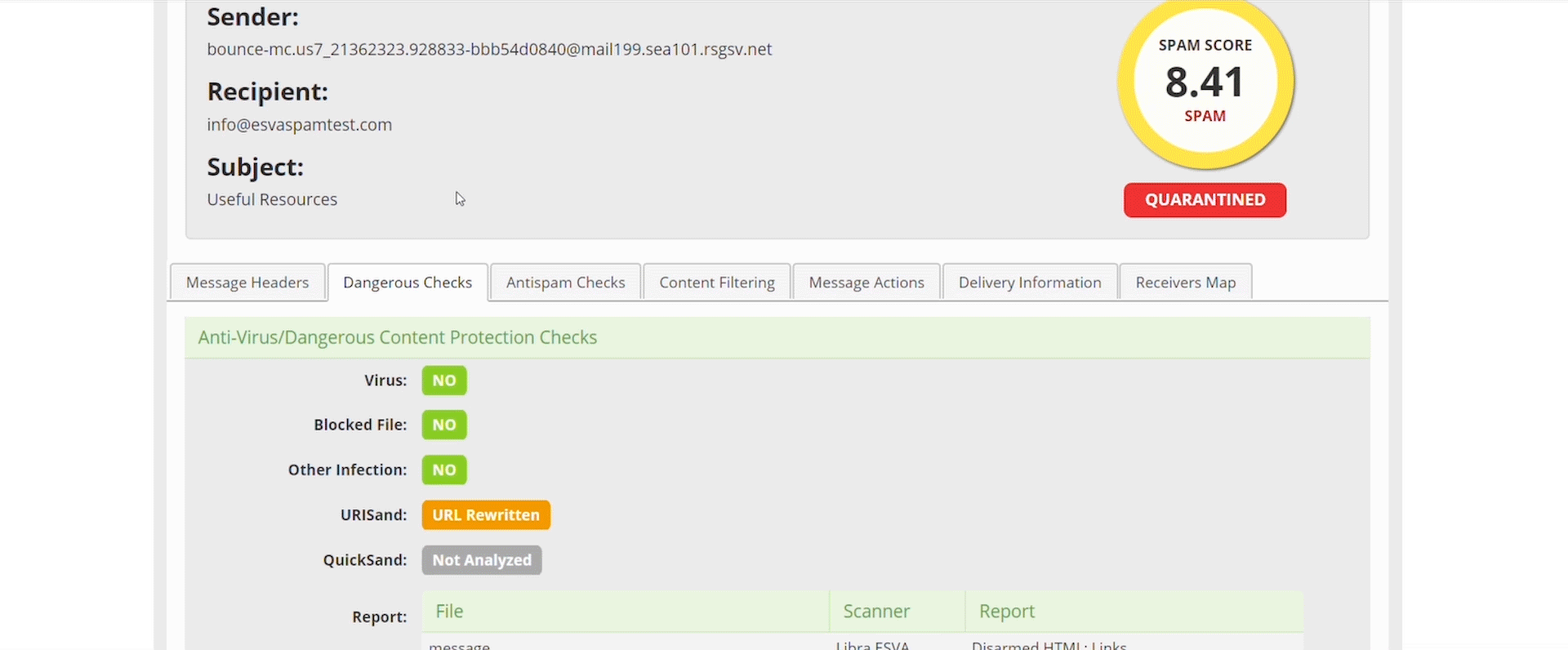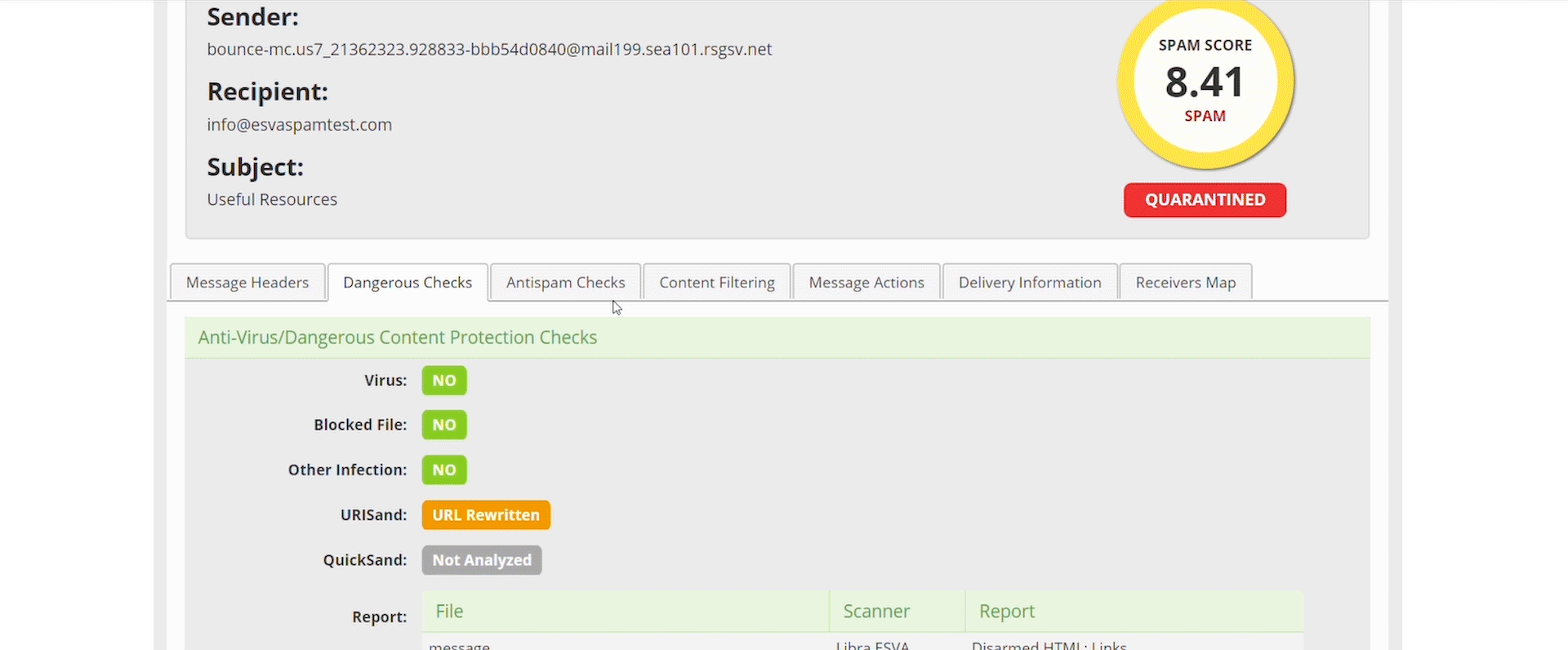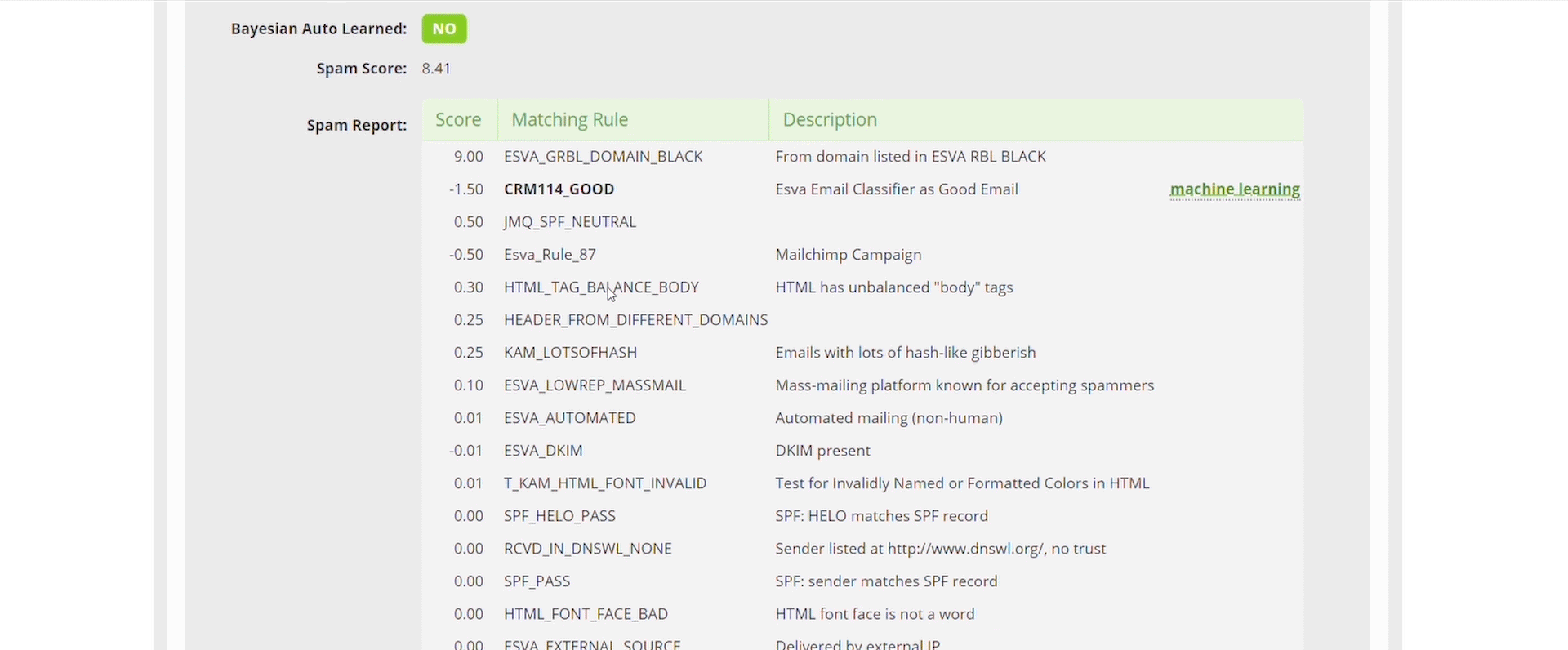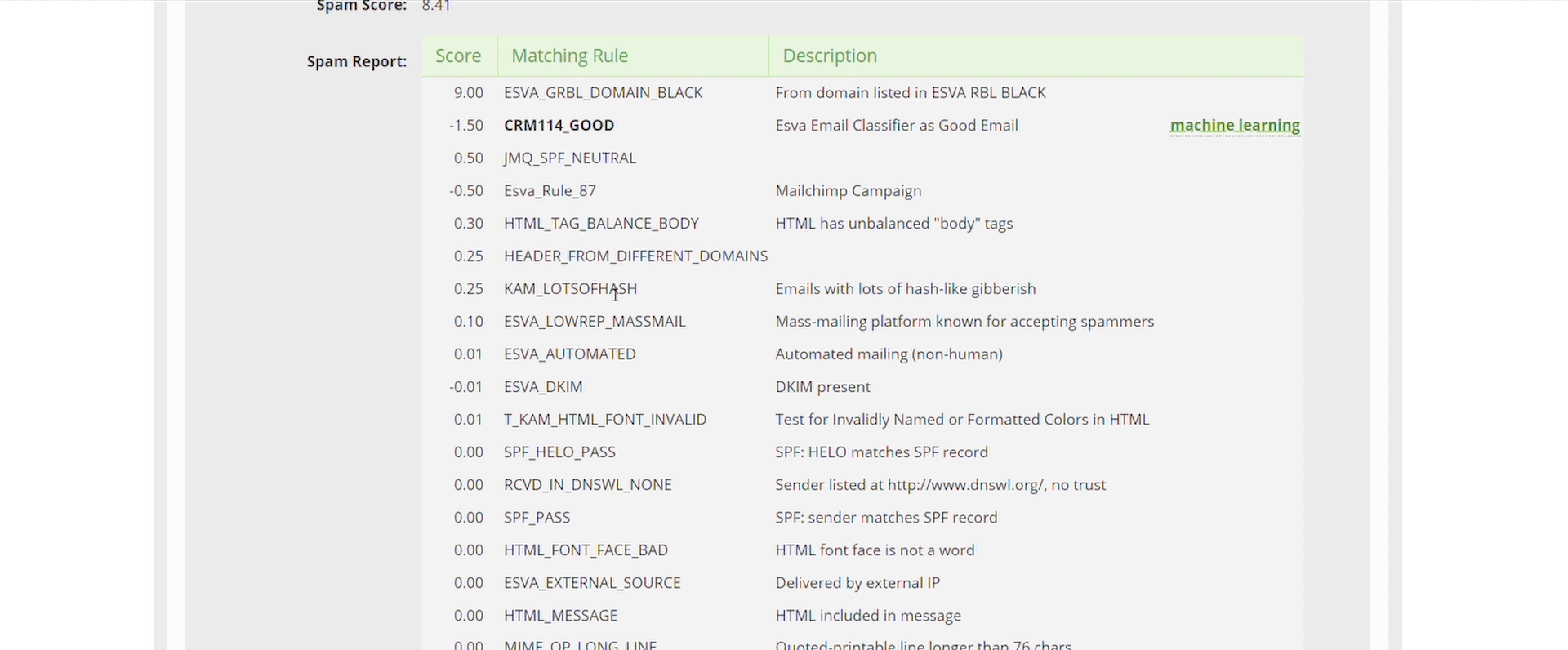
- Always check the Technical Message Details
The first place you should always be checking is the Message Technical Details section, here you can find the Dangerous checks and the Anti-Spam analysis, in these sections you will find all the information and rules that were parsed against the email you are analysing. You can see all of the anti-spam rules, QuickSand and URLSand status and even Virus Signatures.
We want administrators to understand completely and transparently why we did or didn’t block something, if we are wrong then you can tell us, if we are spot on, you now know exactly why we stopped a threat or email.
- Threat Remediation is here for you
If you’re one of the lucky ones who are on Office 365, Exchange or Zimbra email servers, you have unadulterated access to Threat Remediation, a free tool used in the event of a categorisation fail on Libraesva’s side, if something slips past Libraesva, which rarely happens, you can jump into the reports section and immediately remove the threat or unwanted email from your user’s inboxes.
You have a few options after you’ve re-mediated the threat, you can analyse it yourself using number 2 and then if you deem the email to be safe, you can simply release the email back to your users.
- Recipient Verification handles Licensing
So licensing isn’t that complicated in Libraesva, but here is a quick rundown,
Libraesva ESG Yearly Subscriptions licenses unique email addresses, this means aliases, mailboxes, distribution lists and all other unique email addresses will take up a license, Secondly a license is only consumed when Libraesva accepts mail on its behalf and scans it.
So if you don’t verify or validate who the recipients are within your organisation, Libraesva will accept email to any address that is referencing your domain, an example:
[email protected] doesn’t exist, but Libraesva ESG will accept this email and scan it because the system isn’t verifying recipients, thus using a license. So always remember to switch this on, link the ESG to your LDAP or O365 system and validate those recipients! A full guide on how to link LDAP or O365 can be found here and here respectively.
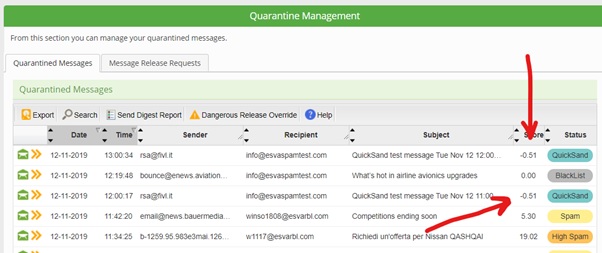
- QuickSand’s sanitised files can be recovered
When you look into your quarantine report at the end of a long hard day you might see something that looks odd, a quicksand message in your quarantine with a score lower than your spam score threshold, don’t panic. This is just telling you that you have the original pre-sanitised and possibly unsafe document, there ready to be released if you need it.
See the way QuickSand works if you aren’t familiar is that it takes active content on PDFs and Office documents and tries to completely remove the content and sanitise the document, leaving you with a plain old PDF or Office document with no content that can cause harm to you or your users, this could be disabling links, removing JavaScript and disabling macros.
However sometimes documents will no longer function, or you might want to access the JavaScript hidden in a PDF for reasons only your organisation know, and we give you that access in the quarantine report.
- In Conclusion
Don’t panic next time you see a quicksand message in the quarantine, these are still getting delivered in a sanitised and safe method, And always remember to leave the heavy security lifting to us and the software, we are here to help make sure the performance of the system is always exemplary.
Thanks for reading! Make sure you follow us on LinkedIn and YouTube for more blogs, videos and other useful content!